Explore my portfolio, a collection of cybersecurity projects that range from malware
traffic analysis and threat hunting to the configuration of diverse home lab environments with
a focus in blue team
operations.
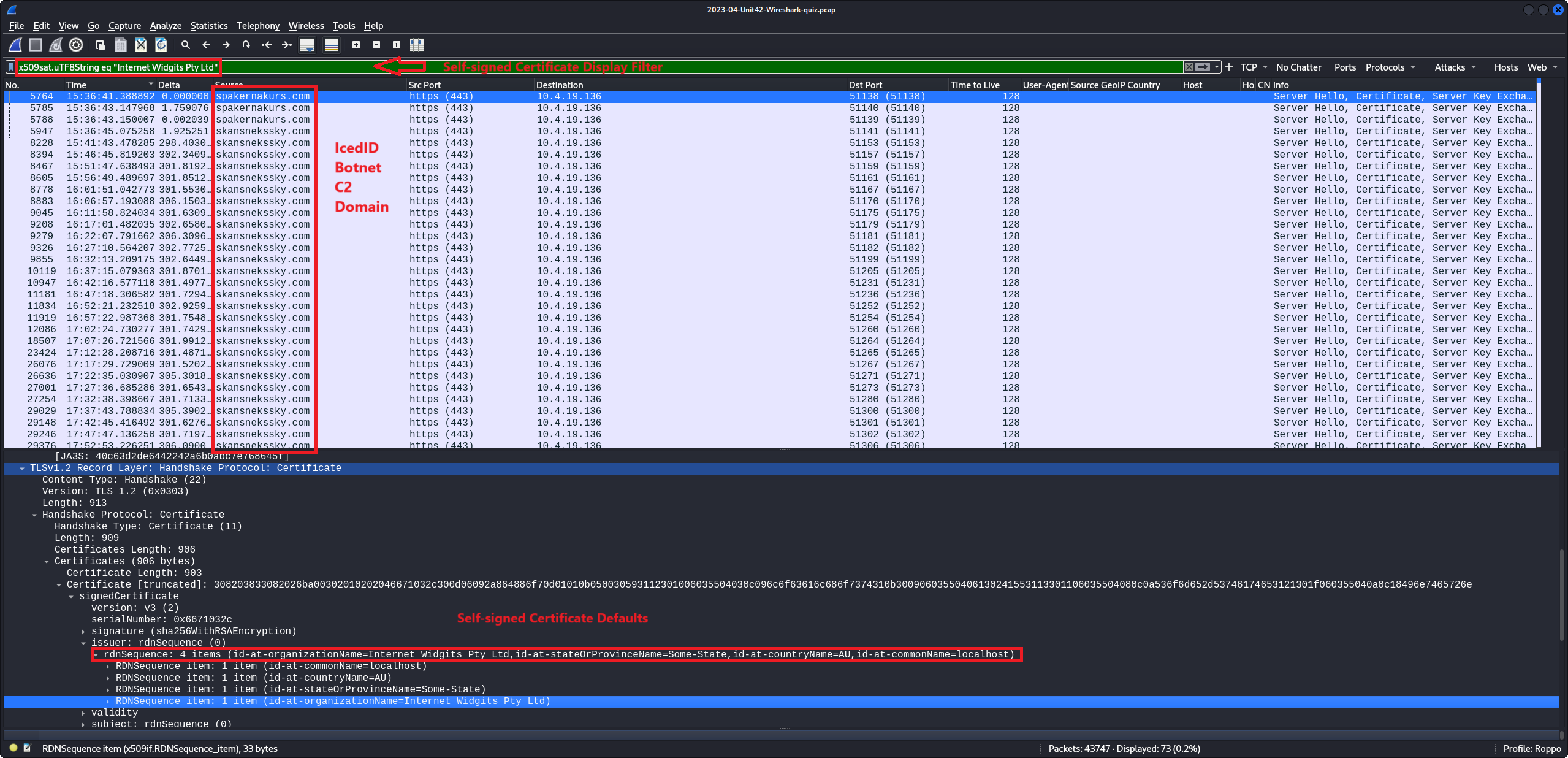
Conducting in-depth network traffic analysis to identify malicious activity, classify IOCs using
threat intelligence, and pinpoint infected hosts across various network environments, resulting
in
comprehensive incident reports.
- Featured Tools -
Packet Analysis: Wireshark, Network Miner
Network Security Monitoring: Security Onion, Zeek, RITA, Suricata
Threat intelligence: Mitre ATT&CK, VirusTotal, URLHaus, MalwareBazaar, Any.Run
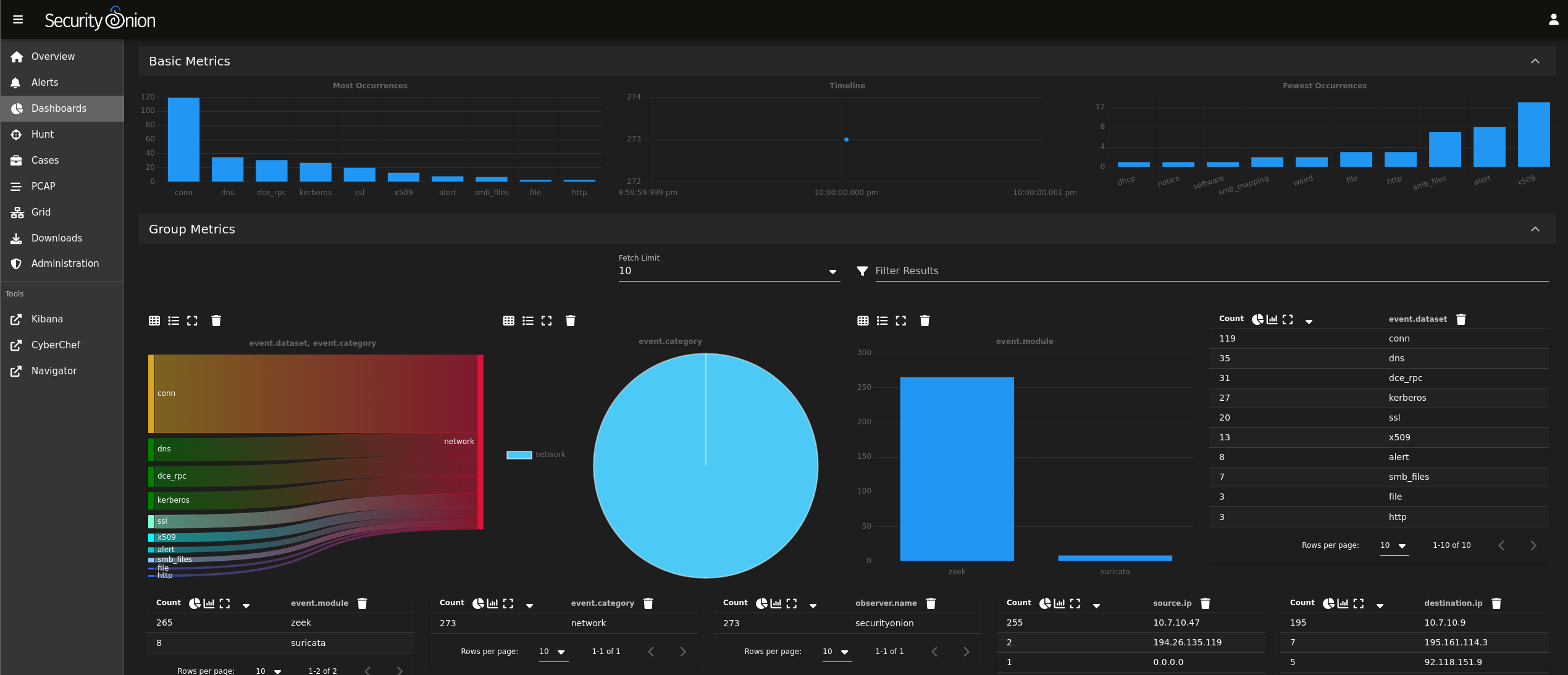
By leveraging various virtualization platforms and operating systems, I deploy and configure
diverse network environments to exercise a versatile skillset ranging from threat detection and
response to vulnerability management and system hardening.
- Featured Tools -
Threat Hunting: AC-Hunter
Vulnerability Scanners: Nessus Essentials
Operating Systems: Windows, Kali, Kali Purple, Security Onion, Ubuntu
SIEM & EDR Solutions: Wazuh, Sentinel, LimaCharlie
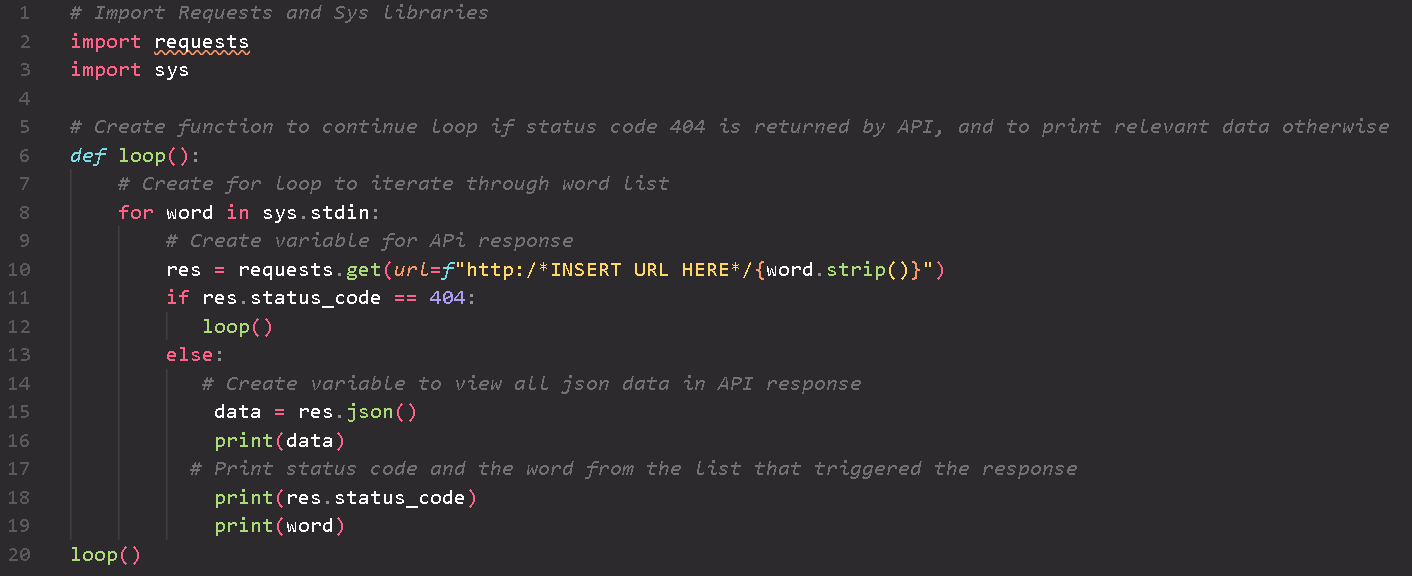
A collection of Python, PowerShell, and Bash scripts designed to automate various networking,
forensics,
threat hunting, and penetration testing tasks, as well as simulate the functionality of
malicious tools
employed by threat actors.
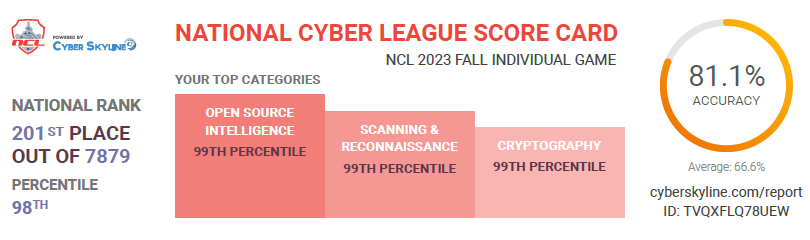
Scouting and performance reports from various CTF competitions showcasing proficiency in skills
such as
Open Source Intelligence, Cryptography, Password Cracking, Log Analysis, Network Traffic
Analysis,
Forensics, and Web Application Exploitation.



