A Malware traffic analysis exercise from a PCAP posted on Malware-Traffic-Analysis.net on
2020-05-28 by Brad Duncan (Unit 42) featuring Redline Stealer malware.
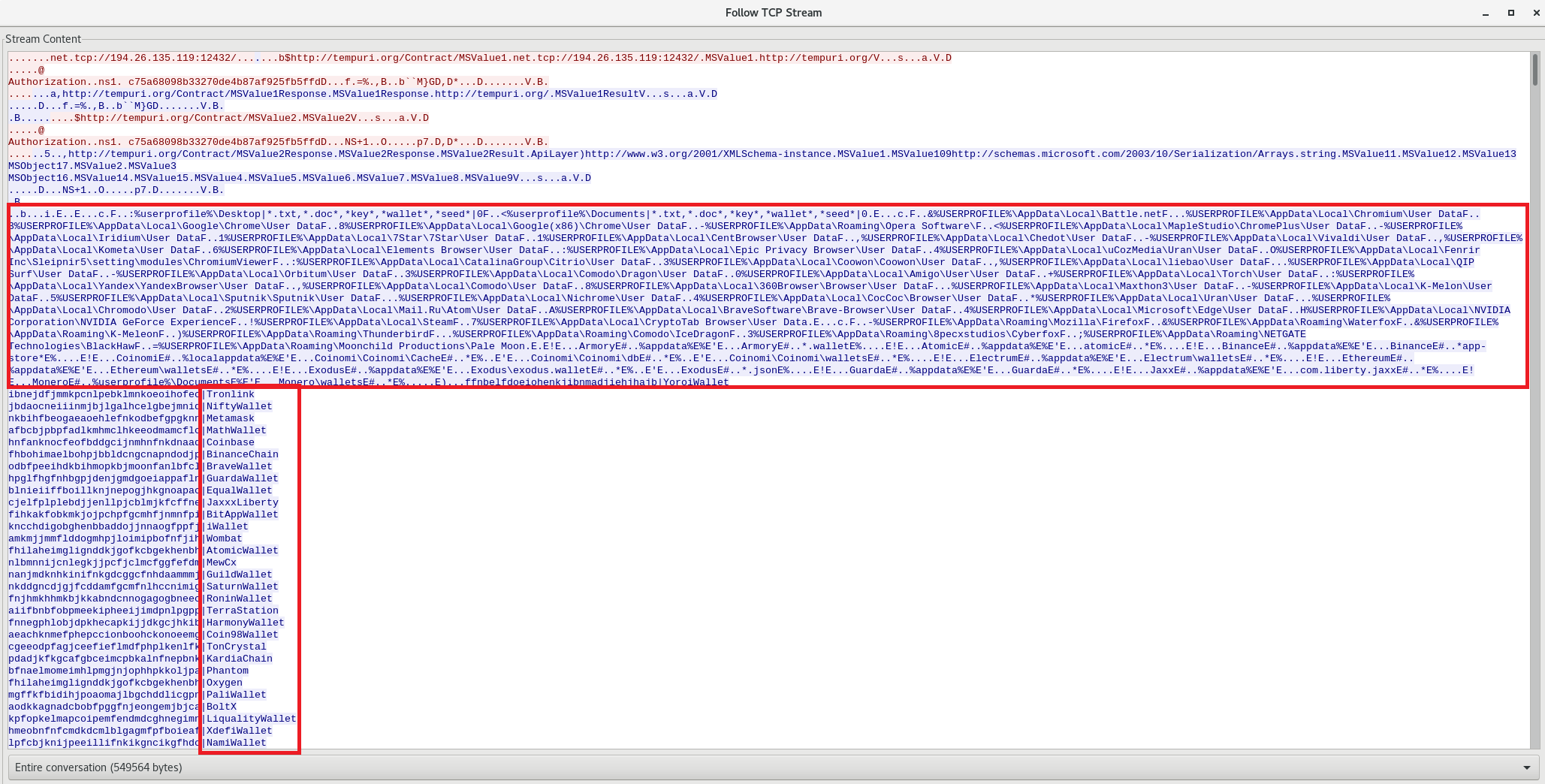
Redline-Stealer is a Windows-based malware categorized as an information stealer. It is
designed
to infiltrate systems covertly and exfiltrate sensitive information, including login
credentials, cryptocurrency wallets, personal data, and other valuable information to remote
command and control (C2) servers operated by threat actors.
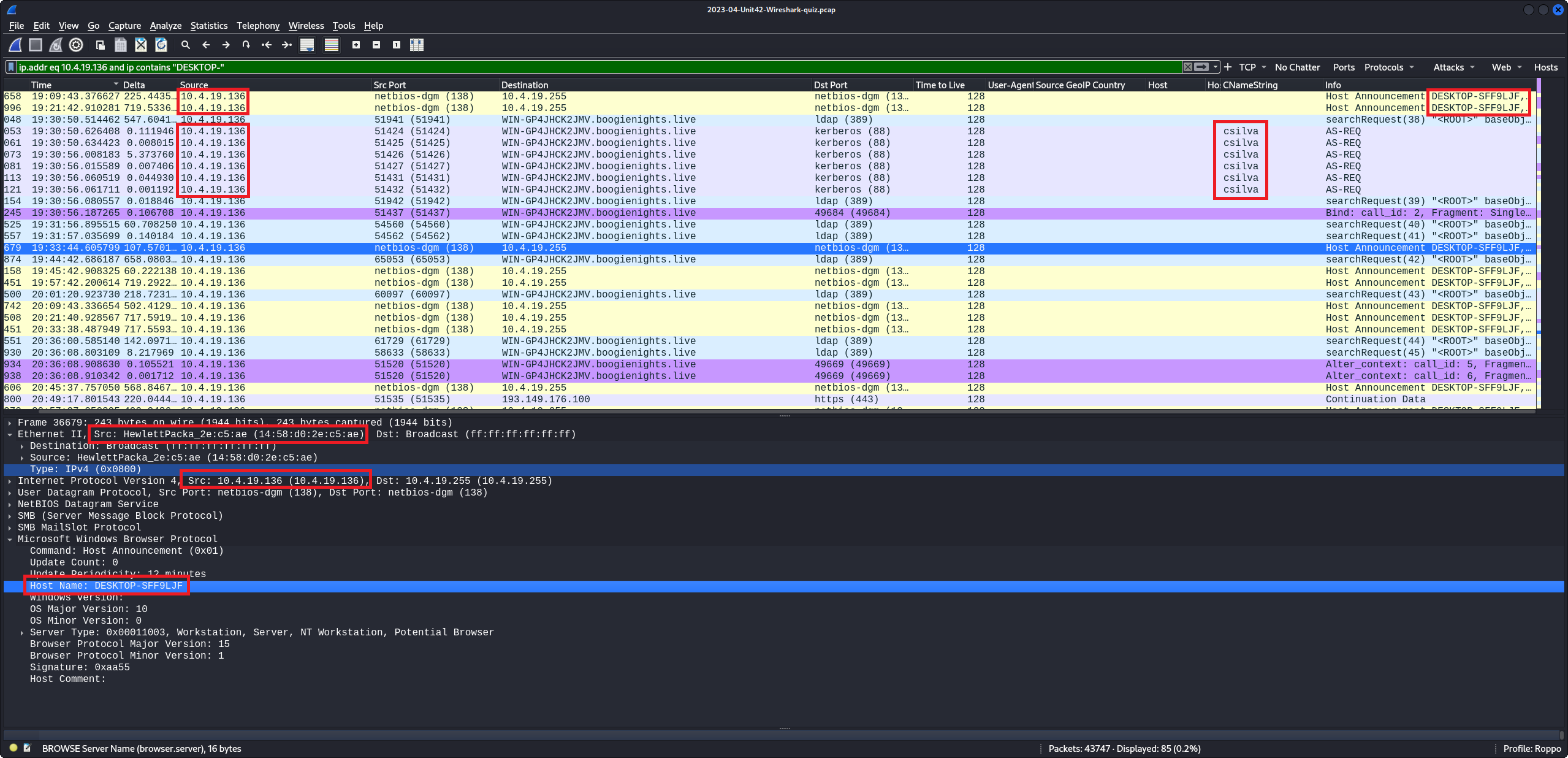
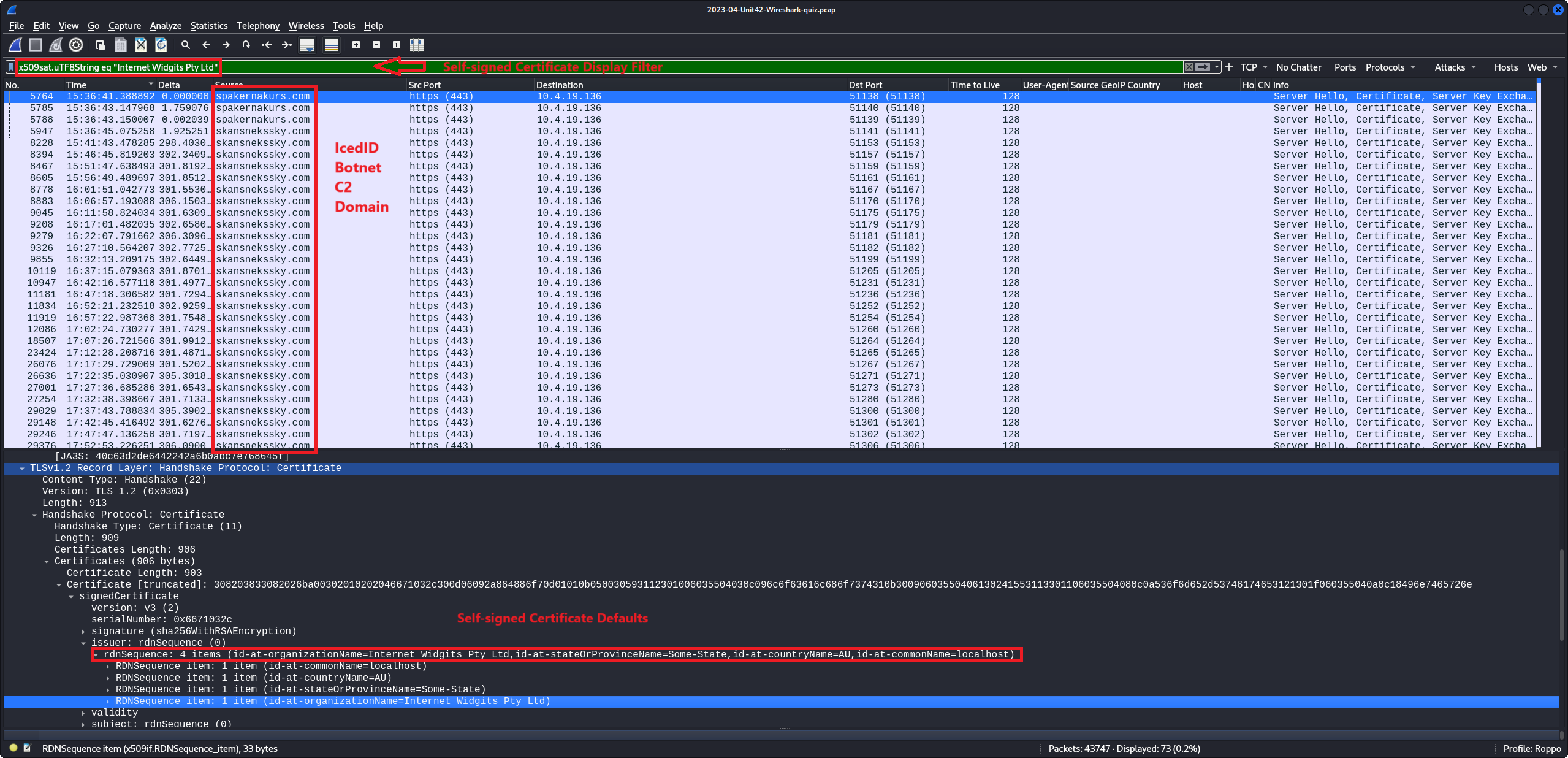
A Malware traffic analysis exercise from a PCAP posted on Malware-Traffic-Analysis.net on
2023-05-26 by Brad Duncan (Unit 42) featuring IcedID malware.
IcedID is a sophisticated banking trojan goes beyond traditional trojans by incorporating
features commonly found in information stealers and modular malware. It is designed to steal
sensitive financial information, login credentials, and other personal data from infected
systems. IcedID is often distributed through phishing campaigns, malicious email attachments,
and exploit kits.
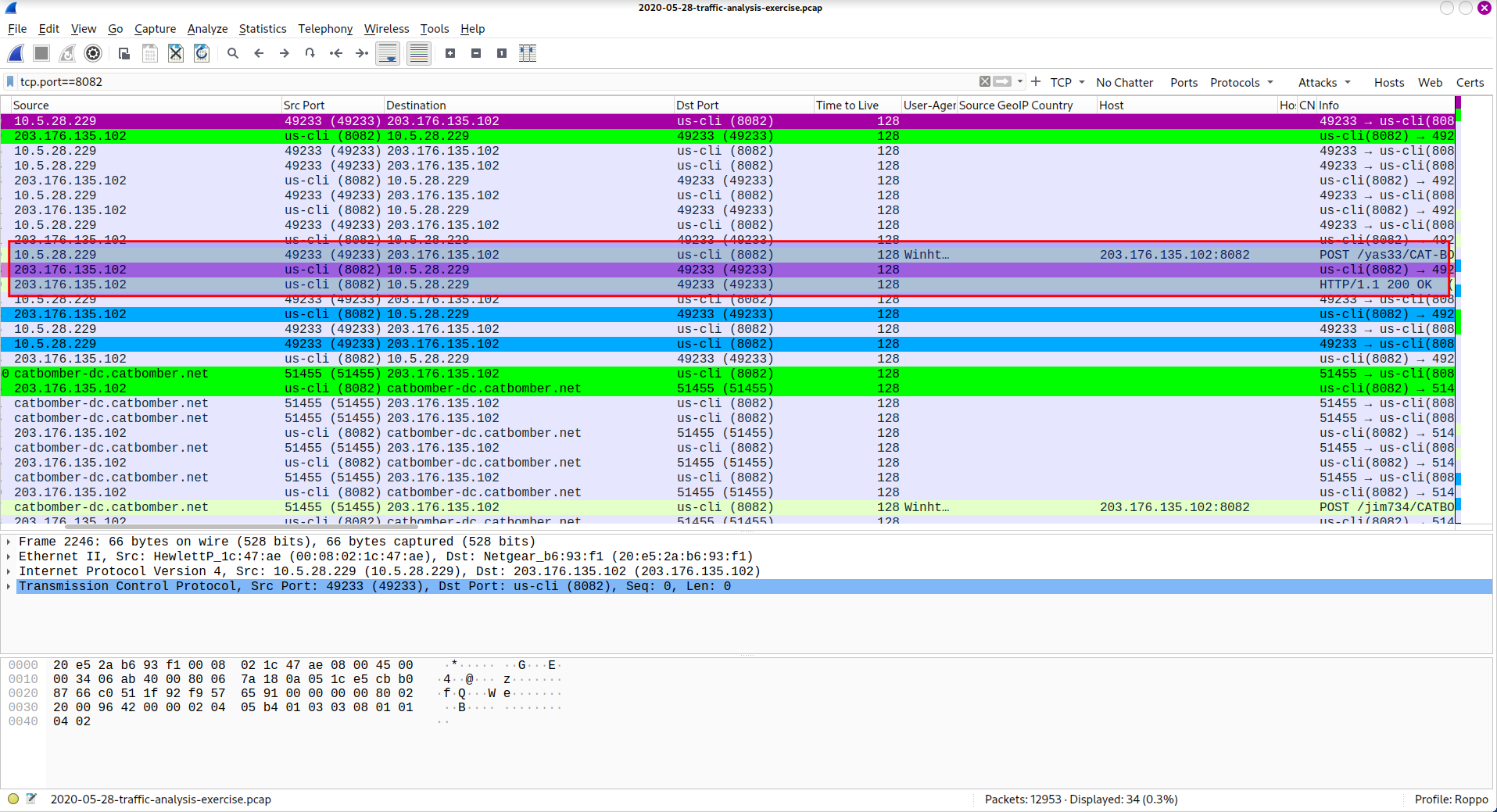
A Malware traffic analysis exercise from a PCAP posted on Malware-Traffic-Analysis.net on
2020-05-28 by Brad Duncan (Unit 42) featuring Trickbot malware.
Trickbot is a type of malware that primarily functions as a banking Trojan to steal sensitive
financial information from infected systems that typically is distributed through malicious
email attachments, phishing campaigns, exploit kits, or malvertising. While Trickbot initially
focused solely on banking fraud, it has expanded its targets to include various industries such
as finance, healthcare, manufacturing, and critical infrastructure since 2016.
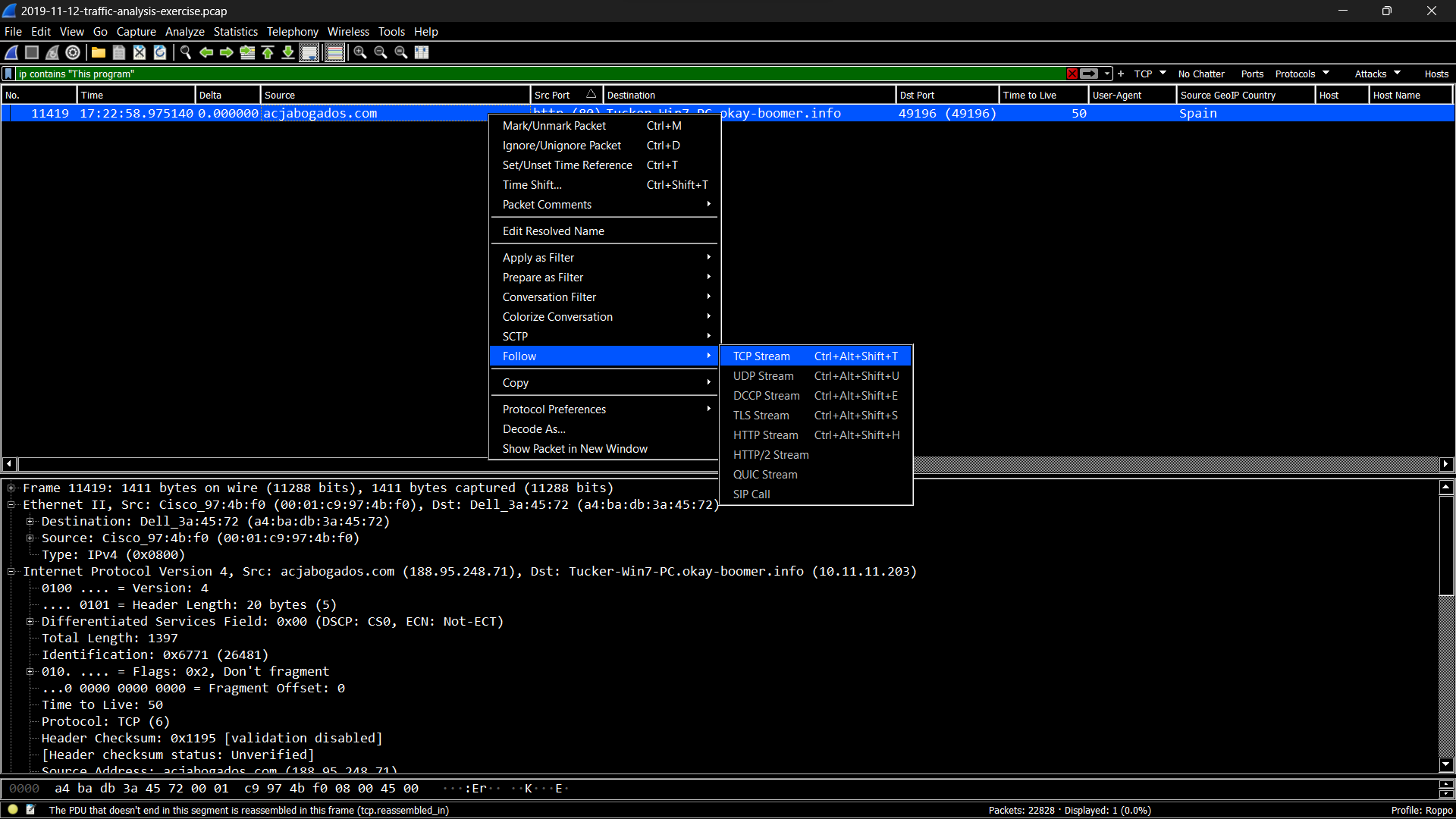
A Malware traffic analysis exercise from a PCAP posted on Malware-Traffic-Analysis.net on
2019-11-12 by Brad Duncan (Unit 42).
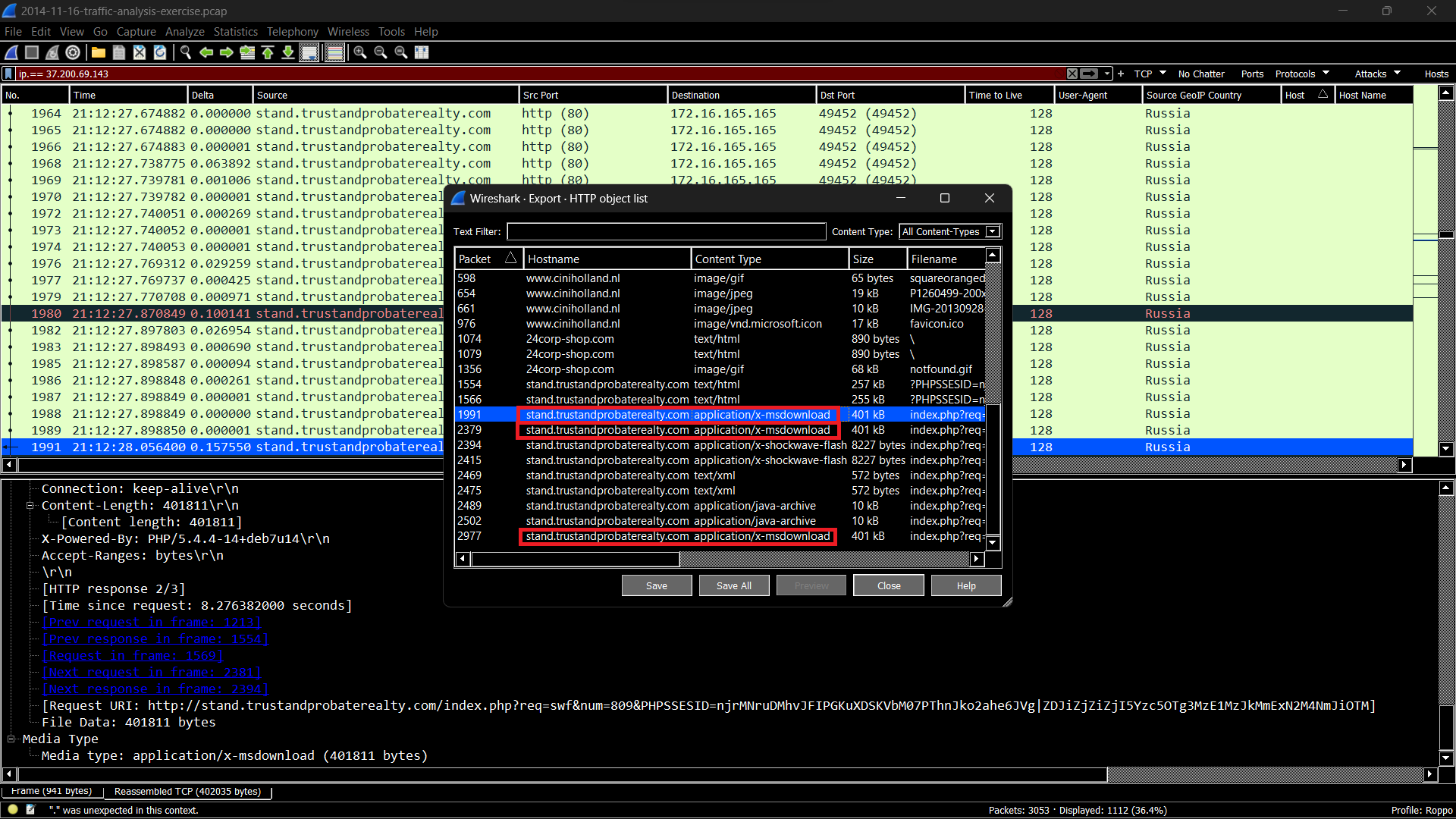
A Malware traffic analysis exercise from a PCAP posted on Malware-Traffic-Analysis.net on
2014-11-16 by Brad Duncan (Unit 42) featuring Rig Exploit Kit malware.