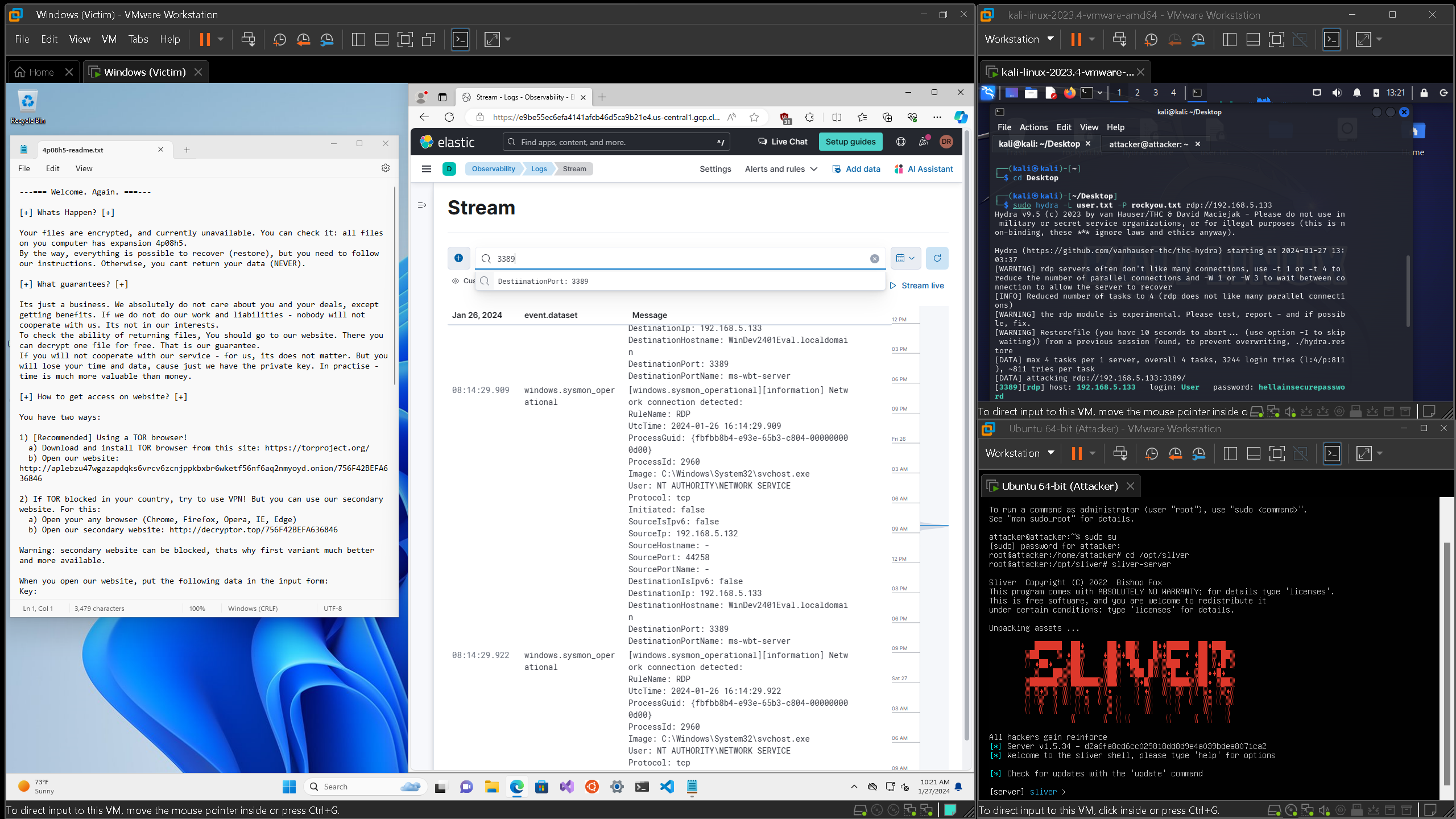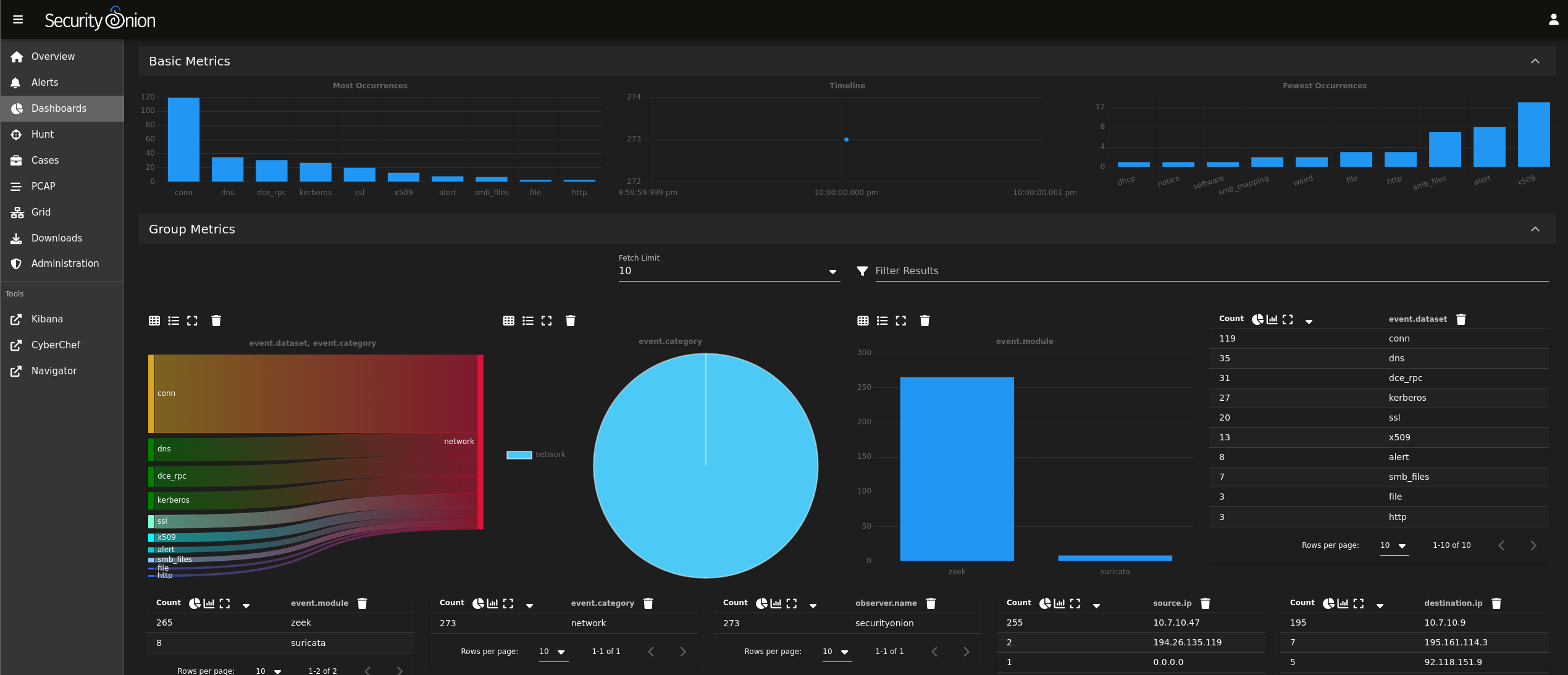
Deployed and configured Security Onion on VMware Workstation Pro, employing Security Onion
Console, Network Miner, Wireshark, MITRE ATT&CK, and Virus Total for malware traffic analysis
and threat hunting. Investigated alerts, identified malicious traffic, extracted Indicators of
Compromise (IOCs), and pinpointed infected hosts in Windows Active Directory, culminating in a
comprehensive incident report.
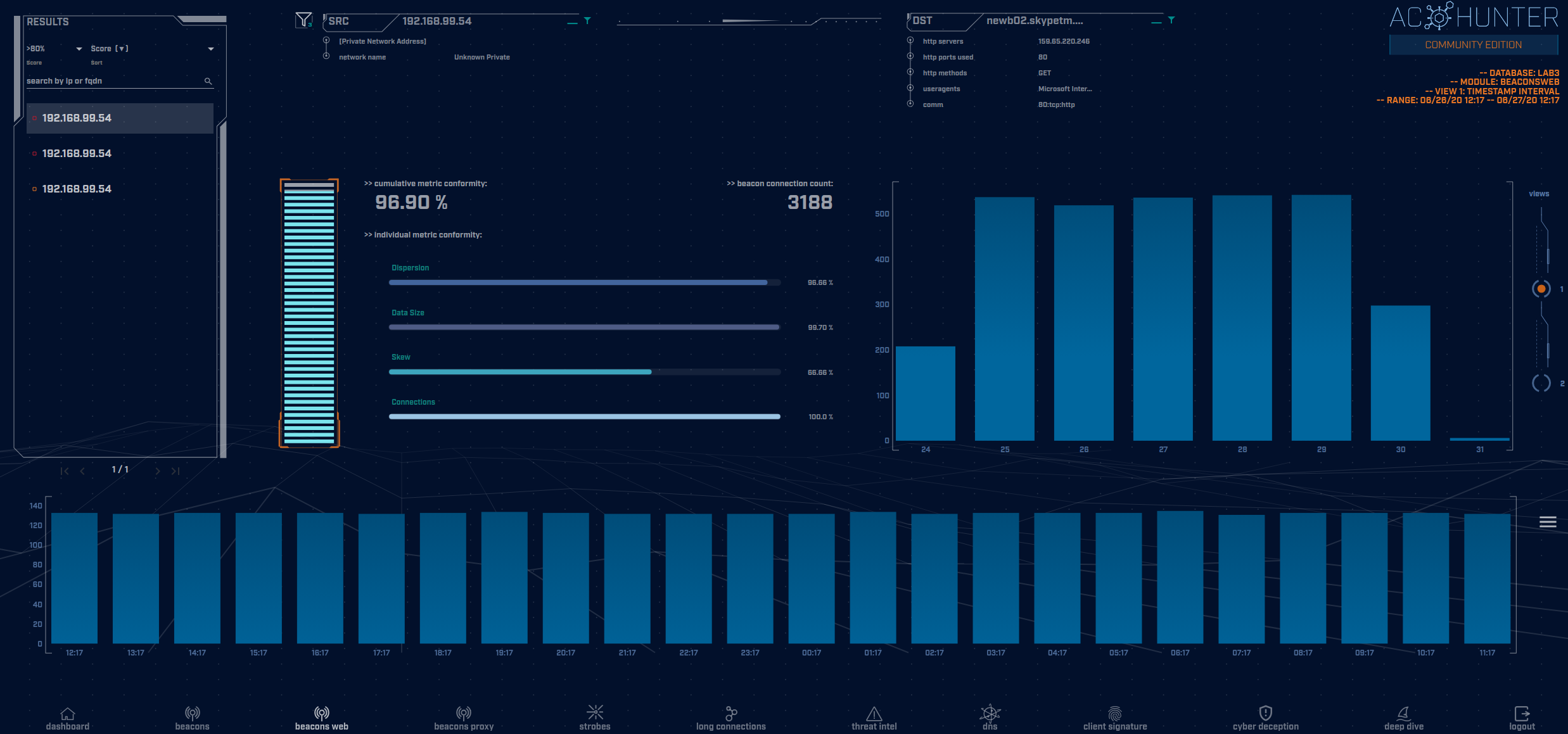
Applied Active Countermeasures' AC-Hunter to proactively search for and identify
potential security threats and adversaries within an organization's
network infrastructure. Unlike traditional measures that rely on
automated security tools to detect known threats, threat hunting involves human-driven
analysis to uncover unknown threats that may evade detection by
automated systems.
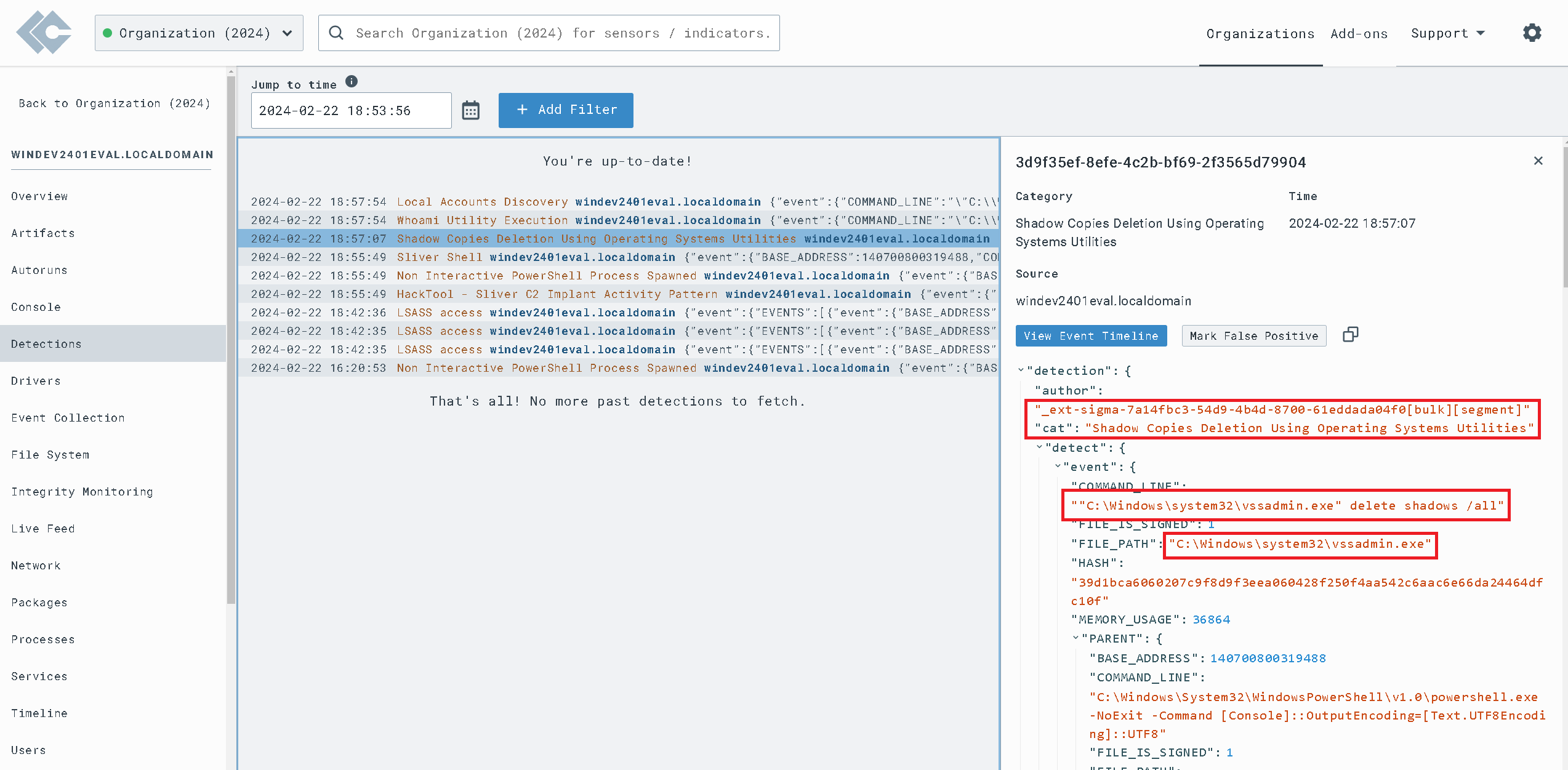
Configured a virtual environment using VMware, featuring an attacking Ubuntu Server VM and a
vulnerable Windows 11 VM. Installed a LimaCharlie EDR agent on the victim endpoint, generated
attack telemetry using offensive tools like Sliver C2 on the Ubuntu Server, observed the
telemetry in the LimaCharlie web interface, and crafted and fine-tuned detection and response
rules to effectively identify and respond to malicious activity.
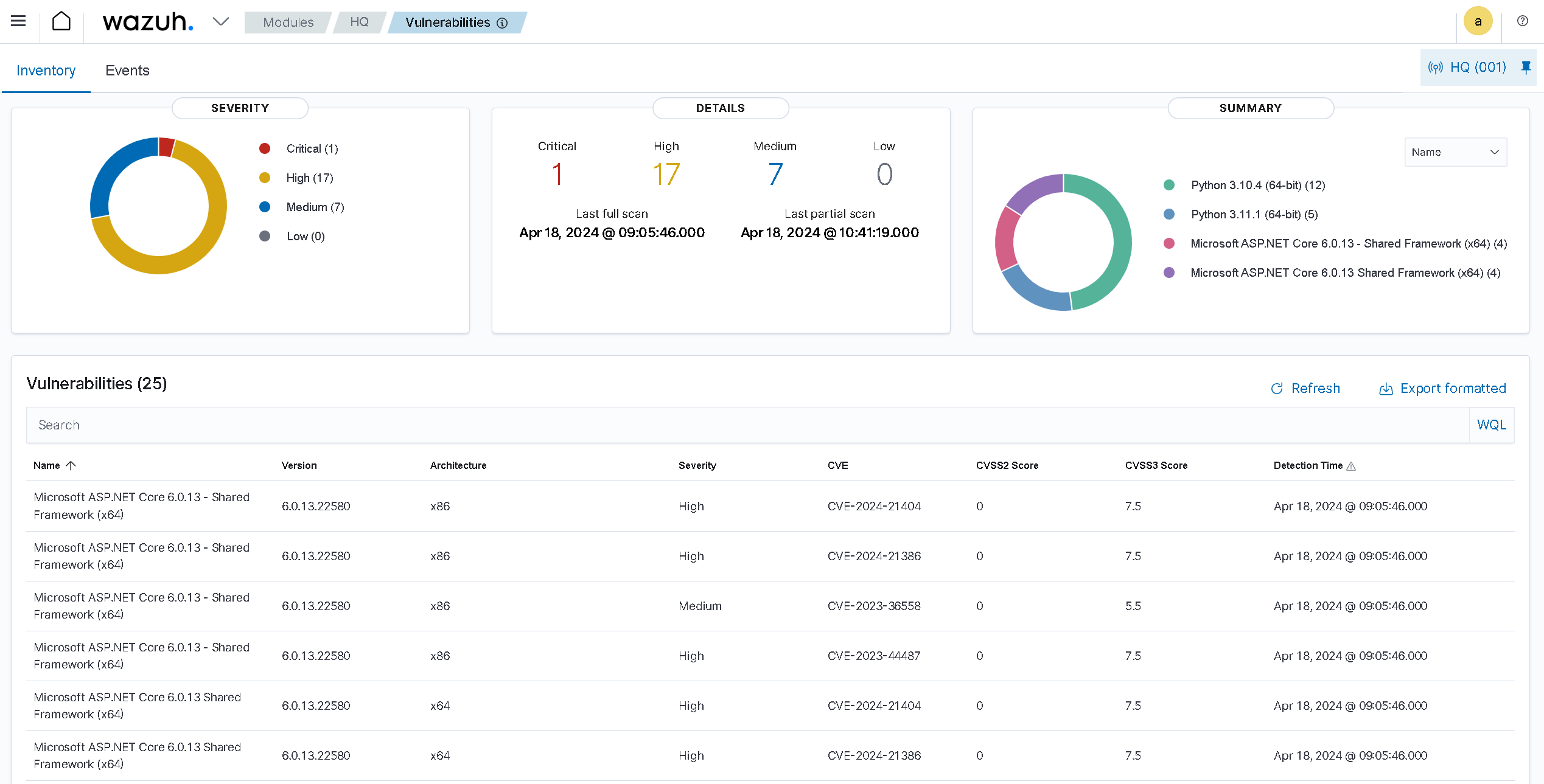
Utilized Wazuh's comprehensive security features to establish incident detection and response
processes,
conduct vulnerability management, monitor file integrity, and harden systems in alignment with
CIS Critical Security Controls.
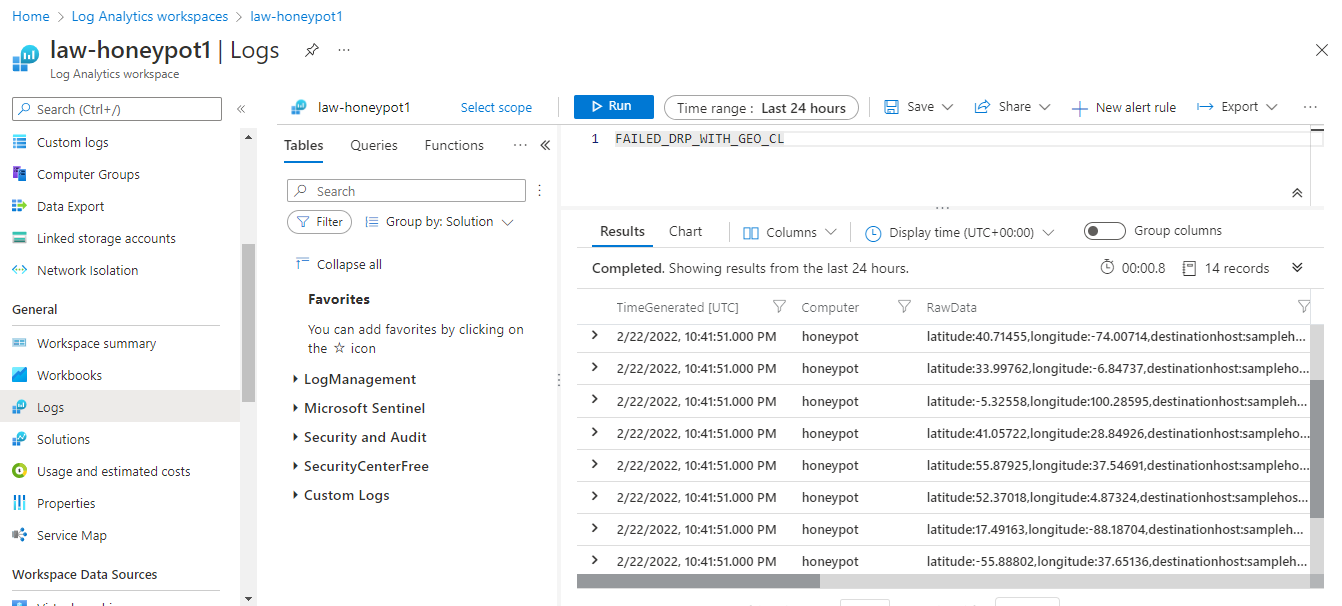
Established a Microsoft Sentinel SIEM lab using Azure VMs and Log Analytics Workspace, connecting
it to a Windows 10 VM serving as a honeypot for actively monitoring incoming global RDP Brute
Force attacks. Employed a PowerShell script using the geolocation.io API to perform
geolocation lookups on attackers, enhancing threat intelligence and mapping capabilities within
Sentinel.
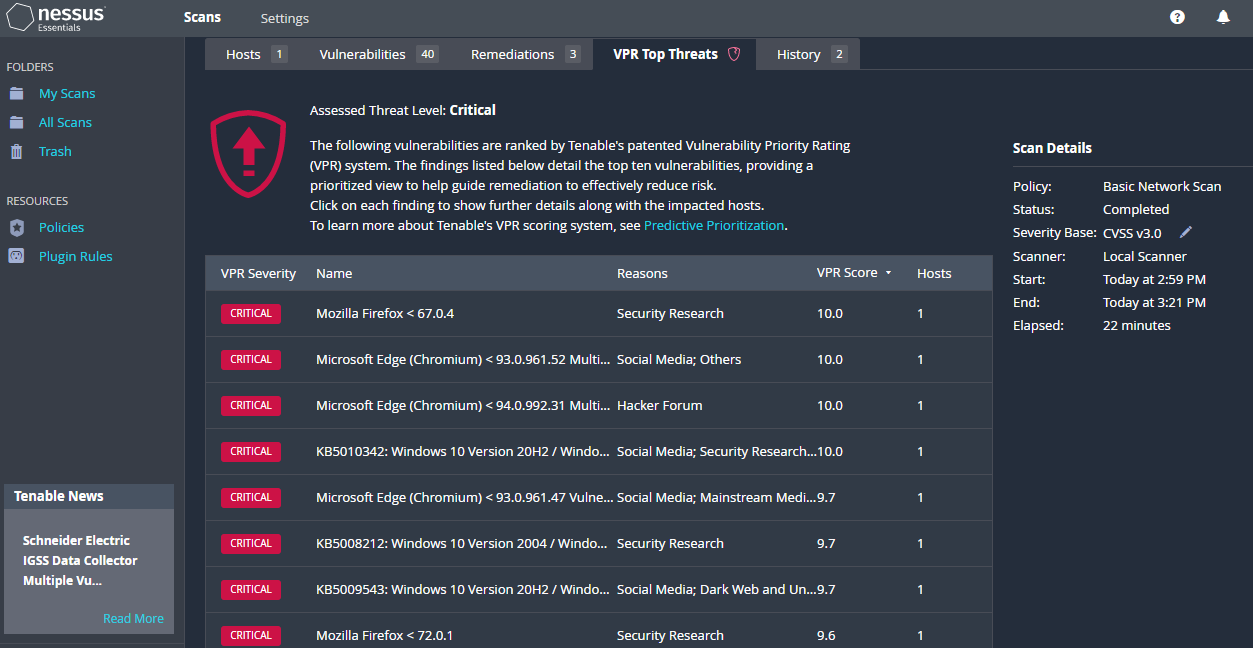
Conducted credentialed scans using Nessus Essentials, identifying and remediating over 150
critical vulnerabilities in a Windows environment, highlighting proficiency in mitigating
security risks in controlled environments.

Authored comprehensive installation guides for Kali Linux, Kali Purple, and Metasploitable
virtual machines, tailored for Oracle VirtualBox and VMWare Workstation Pro platforms,
facilitating streamlined setup and configuration processes for cybersecurity enthusiasts.